 |
|
|||
 |
||||
|
Site Navigation NOC Home
Other links
SoC Homepage |
SSH Tunneling HOW-TOThis information is now unsupported and unmaintained. Or how to tunnel data securely through SSH
Introduction and BackgroundSSH is a program for logging into a remote machine over a secure encrypted communications channel. It is intended to be a replacement for the BSD r* suite of programs (rlogin, rsh, rcp, etc). It can be used as a secure replacement of the telnet program too. In addition, SSH allows you to forward X11 connections and arbitrary TCP/IP ports over the secure communications channel.
Security Concerns of Plaintext Password ProtocolsMany application protocols transmit passwords in the clear or in cleartext equivalent. This means if you use these protocols directly over the network, your passwords could be easily picked up by other users. You might as well had pasted your password in a public place for everyone to see.Some protocols appear to provide encryption but actually only do encoding. For example, the HTTP web protocol provide a Basic Authorization scheme that appears to send your password in a mangled form. This is not encryption, it is only encoding. Encryption and encoding are not the same thing; The latter process is easily reversed. Encoded text is pretty much cleartext equivalent.
SSH TunnelingIn networking terminology, a tunnel is a network connection used to carry or encapsulate another connection. In this case, SSH tunneling means to setup a SSH connection between two computers, and use this SSH connection to carry other application protocols. Even if the application protocols do not encrypt passwords, they are protected because their connection are encapsulated by SSH which provides the encryption. The actual mechanics involves the port forwarding feature in SSH.In port forwarding, you configure your SSH client to forward connections to a local port over the SSH connection, and then onward to a port on a remote server. You'll also reconfigure the application to connect to this local port instead of directly to the remote server.
Port Forwarding Example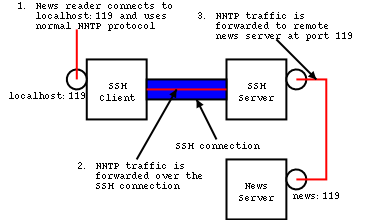 The example on the right shows pictorically how a news reader software,
which does not support encryption, can still connect securely over a SSH
tunnel to a remote news server. The user configures his SSH client to
forward connections to port 119 on his own computer to the SSH server,
and then onward to port 119 on the news server. The news reader software
is configured to find the news server at localhost (or possibly
using the loopback address of 127.0.0.1). When the news reader starts and
tries to access the news server on localhost, its traffic actually
gets carried over the SSH tunnel to the remote news server. The traffic
between the SSH client and SSH server, which might traverse an insecure
WAN, is encrypted by the SSH connection. Traffic between the SSH server
and news server is not encrypted, but this might be lesser of a concern
if they are part of a protected network.
The example on the right shows pictorically how a news reader software,
which does not support encryption, can still connect securely over a SSH
tunnel to a remote news server. The user configures his SSH client to
forward connections to port 119 on his own computer to the SSH server,
and then onward to port 119 on the news server. The news reader software
is configured to find the news server at localhost (or possibly
using the loopback address of 127.0.0.1). When the news reader starts and
tries to access the news server on localhost, its traffic actually
gets carried over the SSH tunnel to the remote news server. The traffic
between the SSH client and SSH server, which might traverse an insecure
WAN, is encrypted by the SSH connection. Traffic between the SSH server
and news server is not encrypted, but this might be lesser of a concern
if they are part of a protected network.
What you need to knowTo successfully setup port forwarding for any generic TCP service, there are a few things you need to know:
Using OpenSSHHere is an example using OpenSSH. OpenSSH is for UNIX based operating systems. The command line for the above example would look like:$ ssh -L 119:newshost.mydomain.com:119 sshhost.mydomain.com The port forwarding setup is specified with the -L option. It takes 3 colon-separated parameters:
You can setup multiple port forwarding by specifying the -L option multiple times. Here is an example that forwards localhost:1110 to pop3host:110 and localhost:3306 to mysqlhost:3306 over an SSH connection to sshhost as user john: $ ssh -L 1110:pop3host:110 -L 3306:mysqlhost:3306 john@sshhost
Using SSH Secure ShellThis section shows you how to setup tunneling using the Secure Shell client from SSH Communications. This is for Windows users. The configuration is based on the port forwarding example above.
| ||||||||||||||||||||||||||||||||||||||||||